
Data leak affects 425,000 Swiss Abroad

Cyber blackmailers have stolen and published what is probably the most comprehensive data set on Swiss citizens abroad. How was this possible?
In mid-May, a stolen data set appeared on the darknet. The content was information about subscribers to Swiss ReviewExternal link. This is a federal government magazine that keeps Swiss citizens abroad up to date on developments in their home country.
The data set is comprehensive. It currently contains over 425,000 addresses, 40% of which are postal and 60% email addresses. Anyone who is registered in Switzerland as a citizen resident abroad automatically receives Swiss Review – either by email or by post. According to the foreign ministry, only 330,000 of the 800,000 Swiss Abroad do not receive Swiss Review – among them, Italian-speaking Swiss.
The Swiss foreign ministry observes all data protection rules in the way it handles these addresses, because this data is not voluntarily submitted; it comes from Swiss consulates abroad.
Anyone who deregisters in Switzerland is obliged to declare their place of residence abroad to the relevant Swiss representation. This creates the subscriber base of Swiss Review.
No access for anyone
The Swiss government considers the data to be so sensitive that not even the publisher of Swiss Review, SwissCommunity, has access to it.
But it is precisely this data set that can now be found on the darknet – or at least parts of it, which exactly is not yet clear. The darknet is the part of the internet that is not accessible to normal computer users.
“The Federal Department of Foreign Affairs has no knowledge of how much data has actually been stolen,” the foreign ministry wrote.
“The fact that data that was not collected voluntarily has been made public in this way is very regrettable,” says Adrian Lobsiger, the federal data protection and information commissioner. He is calling for those affected to be informed.
A criminal complaint has been filed. Cyber experts are investigating.
By-product of a cyber attack
But how could this have happened? Put simply, the 425,000 addresses of the Swiss Abroad are by-products of a blackmail attack on two Swiss publishing houses, the NZZ publishing group and CH Media. The two publishers’ digital infrastructures are networked with each other.
The criminal organisation responsible for the attack calls itself “Play”. It is an internationally active collective of hackers said to have connections to Russia. On May 3, 2023, “Play” published a large amount of data on the darknet that it had stolen from the Swiss publishing group CH Media.
The publication was part of a blackmail poker game, as is common in so-called ransomware attacks by hackers. Their approach is cold and treacherous.
First, the criminals penetrate the IT systems of a company. They then often encrypt their victims’ data. At the same time, they threaten to publish sensitive data. If the blackmailed company refuses to pay the ransom, data records are posted on the darknet.
The attacked companies say they have not paid a ransom.External link
The attack on the digital ecosystem of NZZ and CH Media took place at the end of March. According to editorial director Marc Lettau, the editorial office of Swiss Review also felt the impact of the attack through disruptions to its editorial system. Swiss Review is also connected to the environment under attack via its IT infrastructure.
On May 3, 2023, the day “Play” published the stolen data, CH Media informed its IT customers. The partner companies learned that customer data was also affected. This message was also sent to Swiss Review.
By mid-May, it was clear that the data included the address details of subscribers to Swiss Review. Six times a year, when the magazine goes to print, the Swiss foreign ministry sends this data to the printing company responsible for sending out Swiss Review.
Data protection in the workflow?
Are there data protection measures in this workflow? The foreign ministry’s response: “The dispatch takes place via an encrypted government file transfer. This traffic was not affected, was not hacked and is not the object of the data theft. In accordance with government data protection regulations, this data must be stored in an encrypted form at the printing company.”
It is unclear whether the data set in question was ultimately encrypted. CH Media writes: “We do not comment on individual customer relationships.”
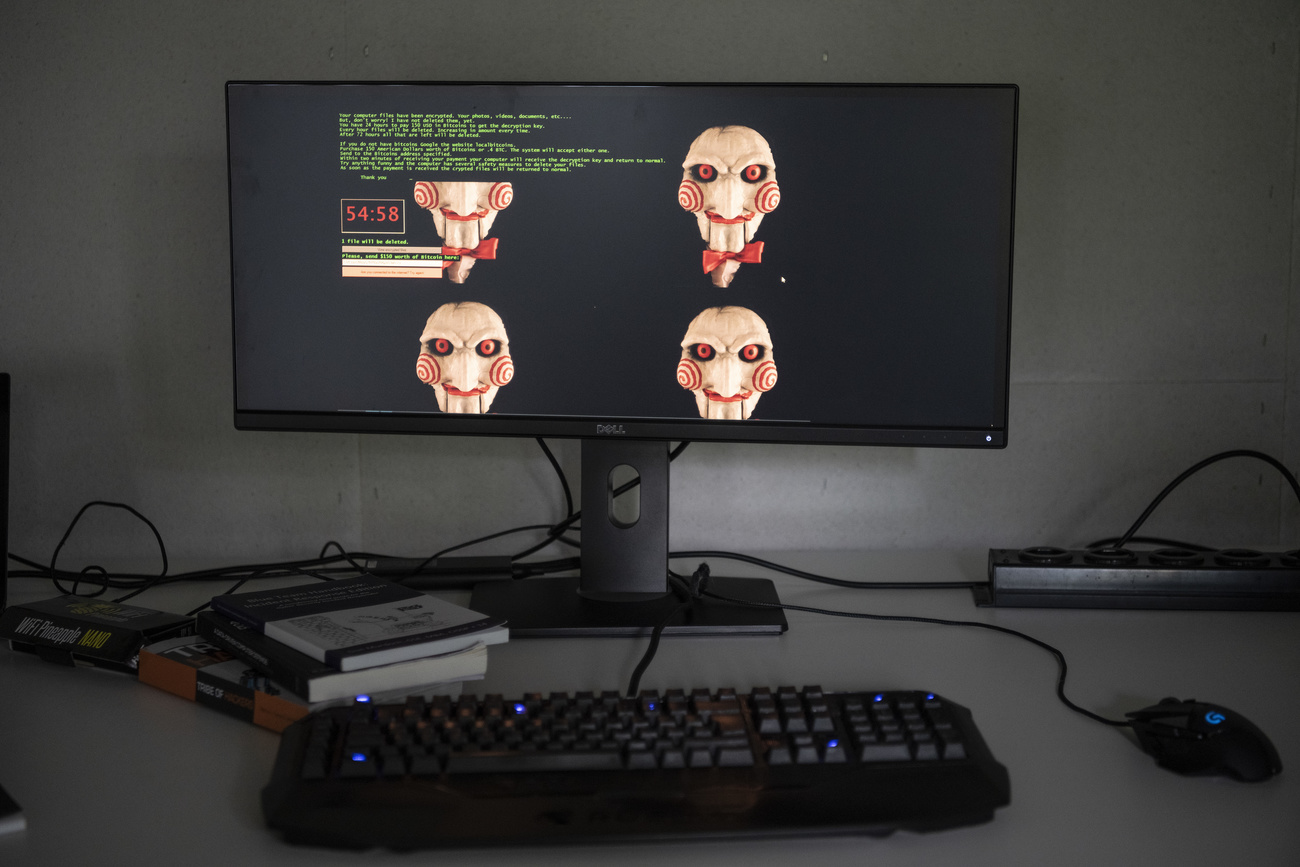
The foreign ministry only issued a statement last weekExternal link, six weeks after the leak became known. The central point in it: apart from addresses, no personal data was in the possession of the printing company.
Clearly the foreign ministry struggled for weeks to come up with a correct assessment and the right communications. But experts are certain: “The fault did not lie with the government,” says Reto Vogt, editor-in-chief of the magazine Inside-IT. The government is known for its sensitive approach to data protection, he says. “This particular case was probably just bad luck.”
E-voting at risk?
However, this attack has the potential to fuel the security debate about the Swiss e-voting system, which was reintroduced in 2023. The first trial of the new system was accompanied by several cyberattacks in Switzerland that attracted attention.
In addition to blackmailing publishers, “Play” also pulled off a spectacular attack on the Swiss IT company Xplain. This company supplies software for Swiss justice and police authorities.
This ransomware attack also resulted in the publication of sensitive data. Among those affected are the army, the Federal Office for Customs and Border Security and the federal police. Investigations are still underway. The extent of the damage cannot yet be ascertained.
At the beginning of June, another hacker collective paralysed important Swiss websites. The attack was carried out by the pro-Russian group NoName and was a reaction to a video presentation by Ukrainian President Volodymyr Zelensky in the Swiss parliament.
Numerous cantonal websites were attacked, as well as websites of the federal government and the Swiss stock exchange. The principle of these attacks was different. Known as DDoS attacks, they consist of orchestrated, mass call-ups of sites that overwhelm them and cause them to temporarily break down.
Neither ransomware attacks nor DDoS attacks are directly related to e-voting technology. However, if such attacks occur frequently, this will have consequences, says IT entrepreneur Franz Grüter. “Even if this incident has no direct connection to the e-voting system, confidence in the security of state IT systems decreases with each additional cyber incident.”
“Dubious security thinking”
For Grüter, the incidents cast a “dubious light on the government’s security thinking”. Grüter is a People’s Party member of parliament and is sceptical about e-voting. He describes the incident as serious and points out that a purchasable data set with all the addresses of Swiss Abroad is particularly valuable in an election year. “Someone could use it for very targeted election advertising.”
The foreign ministry writes that it has “no knowledge of whether the data is currently being offered on the darknet”.

Vogt, however, does not believe the Swiss Review data theft will have a negative impact on the debate about Swiss e-voting. “Both are about the Swiss Abroad, but that’s where the similarities end,” he says.
Psychology, however, should not be underestimated. The Swiss Abroad are not only the biggest lobby for e-voting and e-government, but also the most passionate. This enthusiasm has probably been dampened, because the majority of them have now become victims.
More

In compliance with the JTI standards
More: SWI swissinfo.ch certified by the Journalism Trust Initiative
























You can find an overview of ongoing debates with our journalists here . Please join us!
If you want to start a conversation about a topic raised in this article or want to report factual errors, email us at english@swissinfo.ch.